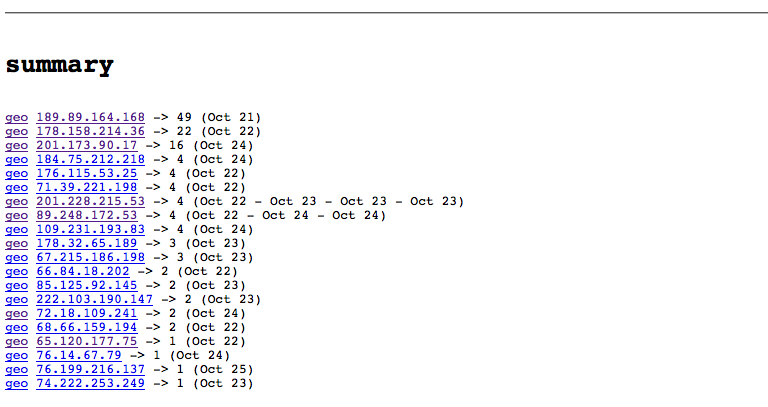
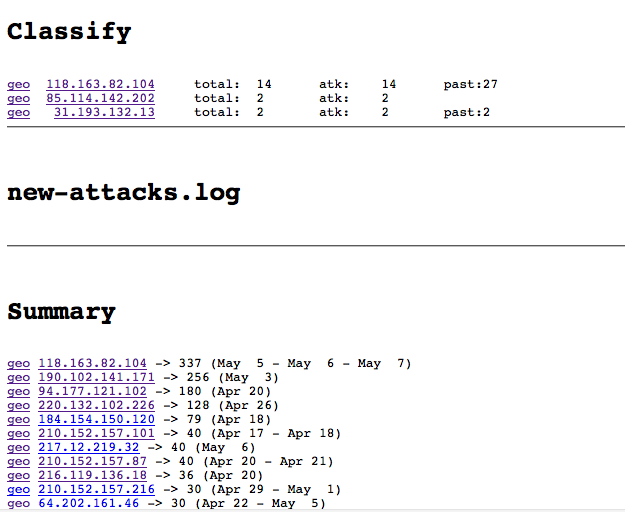
The Dashboard shows visitors and robots
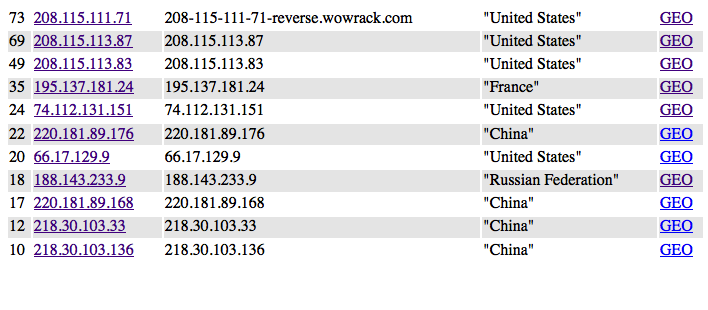
Security Etudes : #100 : Security : IPs
Who is hacking
Plenty of crooks and idiots out there
- For last month some of my websites had been attacked from various places
- I run software on non-standard ports, but it is never a defense from deliberate attack
- Turns out that cloud providers out there don't really care much about crooks using their servers to hack into other people servers
- Last month I've been attacked from GoGrid, HE, Amazon AWS, Webair (not counting Russian and Chineese IPs)
- There are several simple technical steps that ISPs could use to put hackers out of business, and maybe they will do that some day
- In the modern world - if you want to defend your server from hackers - you're on your own
This is what I do now (script does it, on autopilot)
- Look who is trying to hack into my server
- It is as simple as zcat /var/log/* | ips.pl
- Block their IPs with iptables
- This would not protect from DDOS attacks
- Your ISP can protect from DDOS - with a big honking loadbalancer
Why no whitelisting?
- Does not work on port 80
- I generally like to know who exactly is trying to hack into my servers and trace it to the source (hi, little company from Chicago)
Update (Apr 06. 2013)
There is better way.
- Split traffic into 2 groups
- First group - http
- Second group - 'everything else'
- Deal with http attacks in one way and deal with 'everything else' - in another way (based on tcpdump)
Update (May 02. 2013)
https://github.com/kickstarter/rack-attack - looks like a good idea to deal with http group of abusers
Update (Jul 28. 2013)
AutoBan - self-learning intrusion detection system in 100 lines of Perl
March 01. 2013
Background
-
Sony+Hackers+AWS
Amazon.com's Web Services were used by hackers in the April attack against Sony's online entertainment services, according to a Bloomberg ...
-
Detecting TOR Communication in Network Traffic
The anonymity network Tor is often misused by hackers and criminals in order to remotely control hacked computers. In this blog post we explain why Tor is so well suited for such malicious purposes, but also how incident responders can detect Tor traffic in their networks.
-
SNORT
Snort® is an open source network intrusion prevention and detection system (IDS/IPS) developed by Sourcefire. Combining the benefits of signature, protocol, and anomaly-based inspection, Snort is the most widely deployed IDS/IPS technology worldwide. With millions of downloads and nearly 400,000 registered users, Snort has become the de facto standard for IPS.
-
Rack::Attack: protection from abusive clients
If you've looked at web server logs, you know there are some weird clients out there. Malicious scripts probe for exploits. Scrapers download the same page dozens of times each second, or request the 10,000th page of comments for a post with only 2 comments.